Incydr + Salesforce
Nick Winninger, Product Manager at Code42, explains how the Salesforce Exfiltration Detector provides clear visibility into what Salesforce reports employees are downloading.
Customer lists, sales performance forecasts, pricing information—the list goes on. While Salesforce is widely adopted and integral to the success of most organizations, it also represents a high-risk method of exfiltration around which many organizations do not have appropriate data governance.
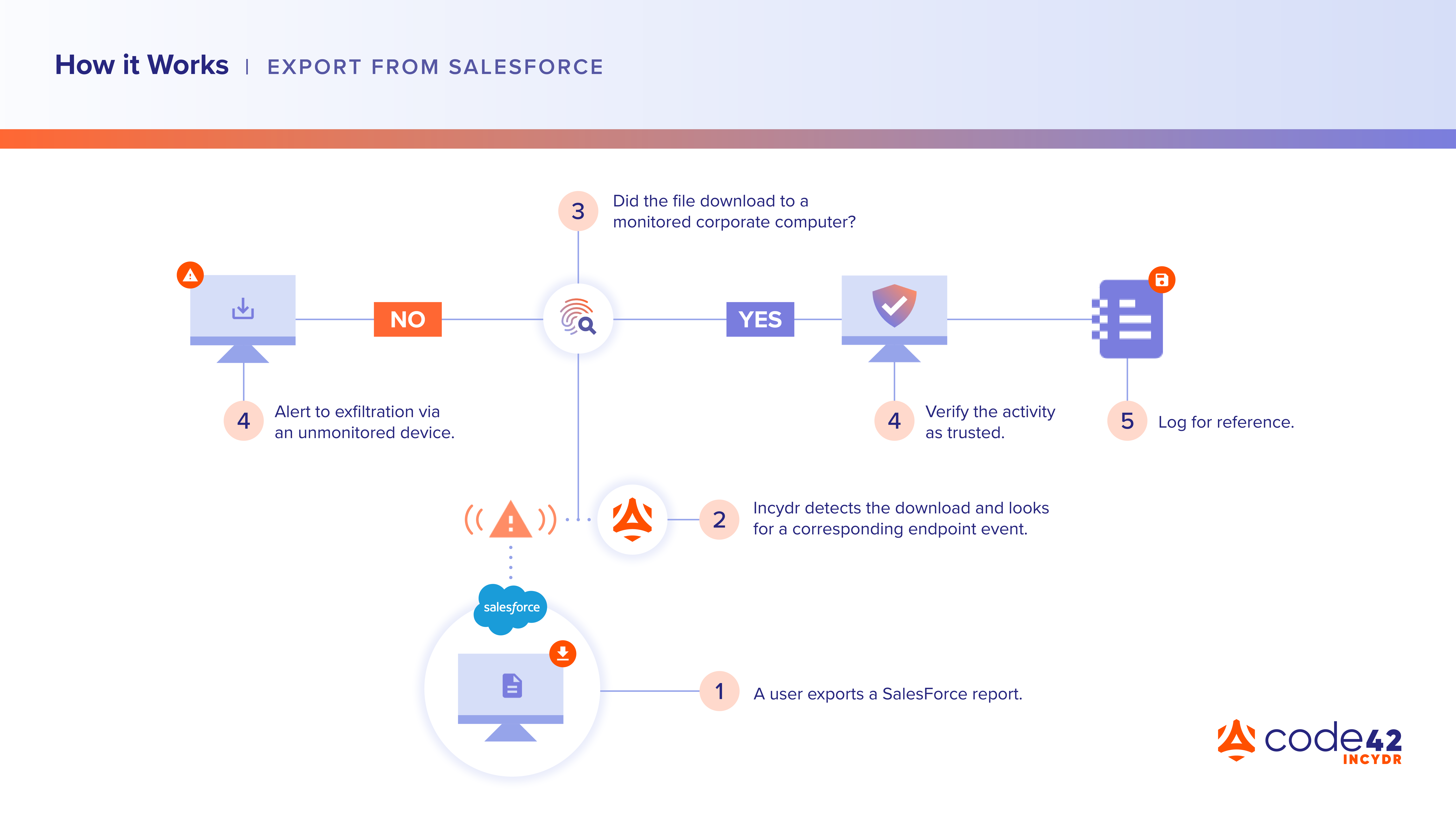
With the Code42 Incydr Exfiltration Detector for Salesforce, security teams can protect confidential and regulated Salesforce data by ensuring Salesforce reports are only downloaded to monitored corporate devices. When Salesforce reports are downloaded to an unmanaged device, such as a personal laptop or mobile phone, security teams are alerted to immediately investigate and act on this activity.
Because the integration is API-based, there’s no additional network layer technology to deploy and manage and it works regardless of network, making it perfect for organizations with distributed workforces.
"Salesforce is one of the largest repositories of customer data we have. Before using the detector, we hired a Salesforce expert to just make sense of the logs. We’re now using this tool to determine where to make changes in our environment and determine mobile device policies. This information has been extremely difficult to interpret for years, until now.”
Tim Briggs, Director of Incident Response at CrowdStrike



Learn why increasing visibility into Salesforce should be a prioritized effort
Reduce noise by intelligently differentiating between sanctioned and unsanctioned activity
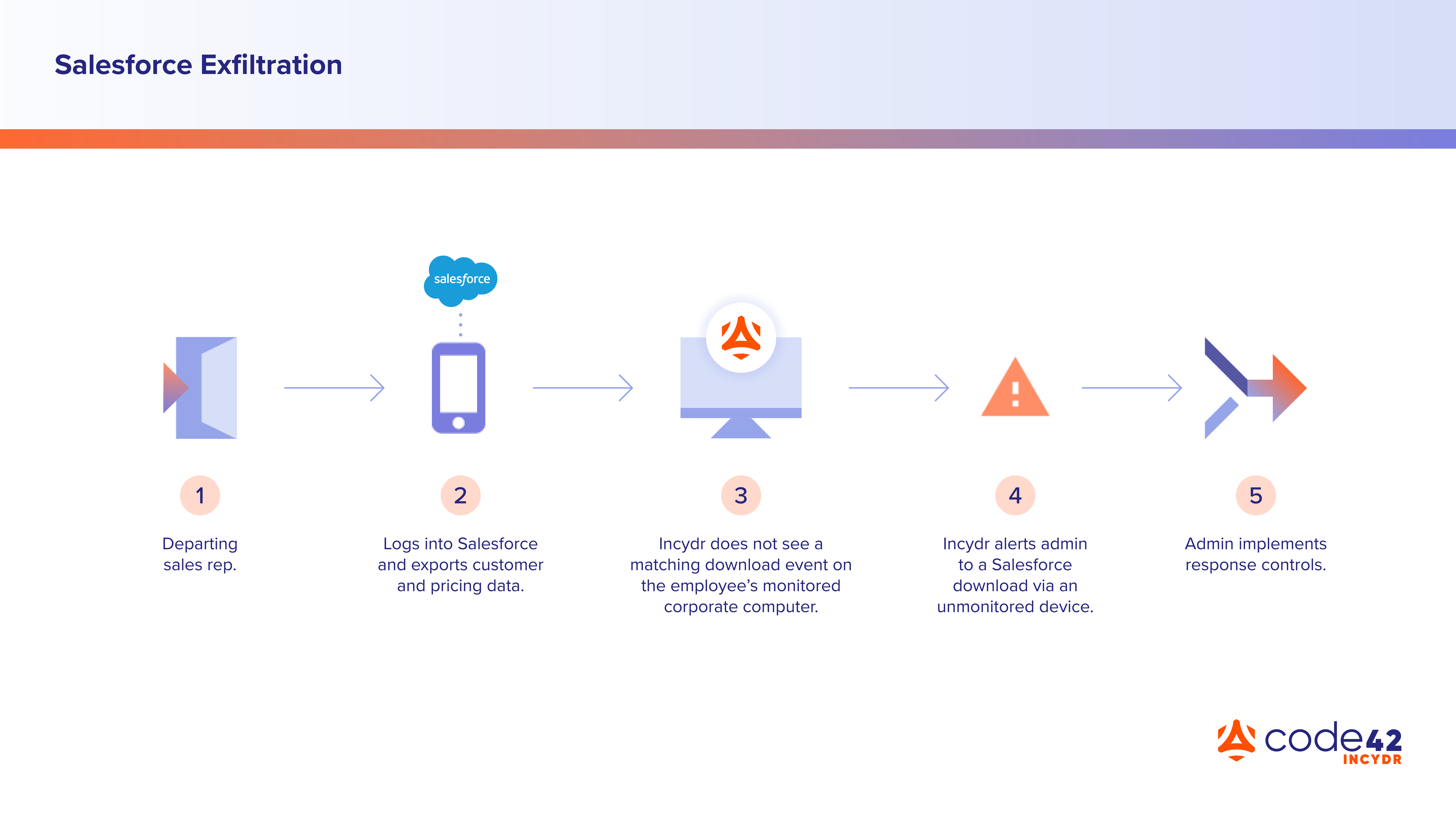
Learn how people, processes and technology worked together to detect when a departing employee downloaded sensitive Salesforce data to a personal laptop