This rising tide of insider threats has set the backdrop for our new book, Inside Jobs: Why Insider Risk Is the Biggest Cyber Threat You Can’t Ignore. With work from home on the rise and data moving off company networks, it’s time to rethink approaches to data security. Get practical advice, proven frameworks for assessing risk and how-to’s for building an Insider Risk program.

Fill out the form below.
Fill out the form below.
lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsumv




lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsumv




Fill out the form below.
View this video to get a quick introduction on Incydr™.
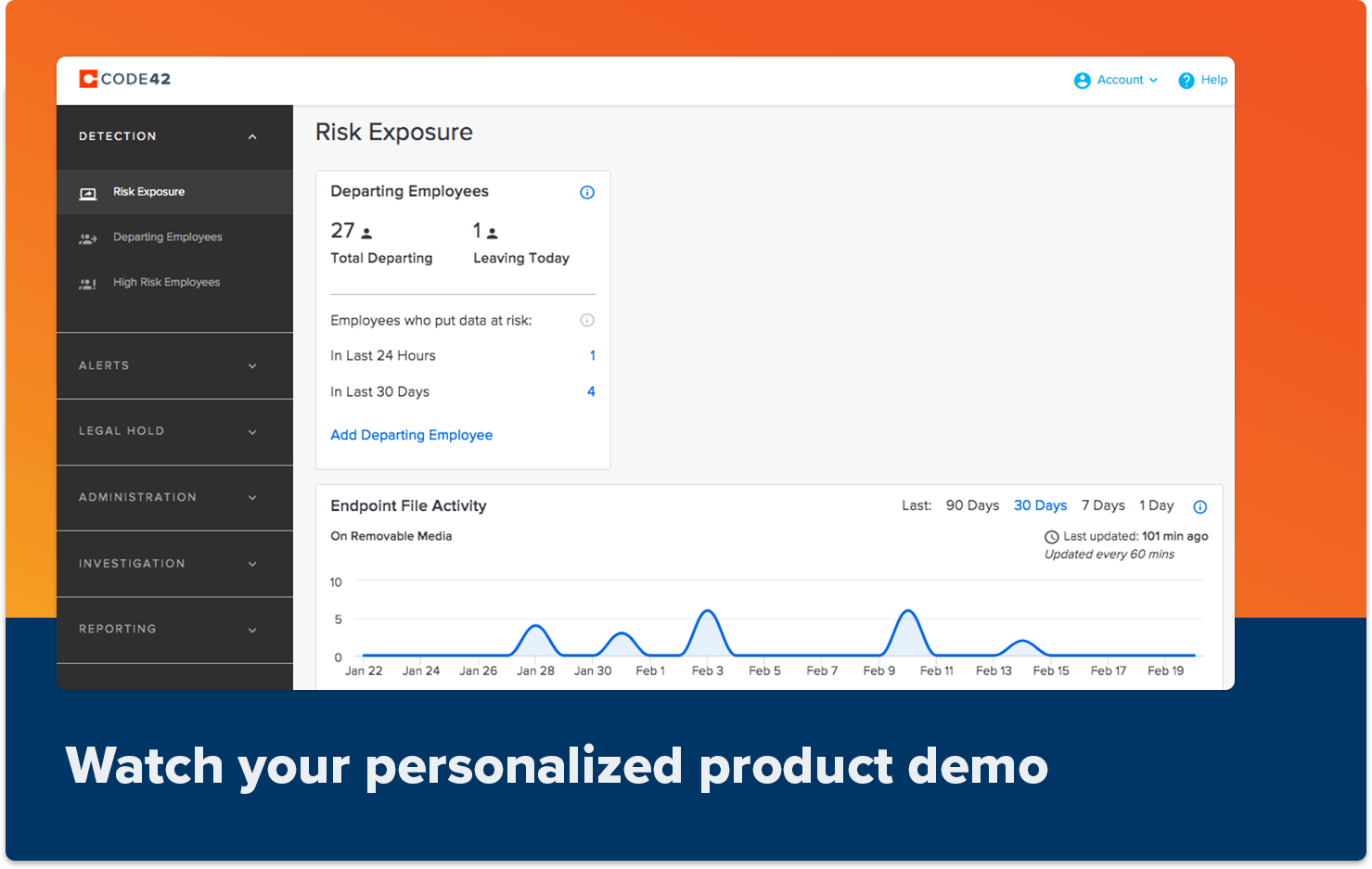
Incydr prioritizes your highest risk users and events so you can clearly differentiate between harmless file movement and true data leak or theft —giving you the context needed for Zero Trust.
When monitoring files, vectors and user Insider Risk Indicators (IRIs), Incydr gives context to data handling activity by users. IRIs are activities or characteristics that indicate corporate data is at risk of exposure or exfiltration.
This allows security teams to verify who and what was done with organizational data regardless of whether the user was on network or off. "Trust" isn't just assumed because a user is logged in, it's continuously verified and inferred, by the context of those activities and the data they involve.
Incydr assigns a numerical risk score to every IRI. These scores are totaled to determine the overall risk of a detected event and its severity. IRI severities allow Incydr and security teams to take a use-case centric approach to Insider Risk Management.
If needed, Incydr administrators can adjust the model to fit their own risk tolerance. Risk settings allow administrators to modify how users and events are prioritized. Incydr’s trust settings tell Incydr what activity it should de-prioritize, like activity with trusted domains. This prevents approved file activity from triggering alerts or cluttering dashboard views.
Code42 partners with leading technology providers your organization is already using, allowing you to automate and streamline incident response processes related to insider data risk.
Detect, investigate and respond to insider threats faster than ever before — with technology you already have.
Detect, investigate and respond to insider threats faster than ever before — with technology you already have.
This rising tide of insider threats has set the backdrop for our new book, Inside Jobs: Why Insider Risk Is the Biggest Cyber Threat You Can’t Ignore. With work from home on the rise and data moving off company networks, it’s time to rethink approaches to data security. Get practical advice, proven frameworks for assessing risk and how-to’s for building an Insider Risk program.


This rising tide of insider threats has set the backdrop for our new book, Inside Jobs: Why Insider Risk Is the Biggest Cyber Threat You Can’t Ignore. With work from home on the rise and data moving off company networks, it’s time to rethink approaches to data security. Get practical advice, proven frameworks for assessing risk and how-to’s for building an Insider Risk program.
Organizations are moving faster than ever before. End users are creating, modifying, deleting data every second, on their laptops and in the cloud. Employees are being onboarded, enabled, empowered and offboarded, all in a remote world. Your security team needs to keep up with these risks, while remaining compliant, and enabling the business. Security tools like DLP, UEBA and CASB aren’t keeping pace. They typically address a single dimension of risk, take months to deploy, and burden security teams with constant fine-tuning. It’s time for a Zero Trust approach to managing and mitigating data risk from insider threats.
Organizations are moving faster than ever before. End users are creating, modifying, deleting data every second, on their laptops and in the cloud. Employees are being onboarded, enabled, empowered and offboarded, all in a remote world. Your security team needs to keep up with these risks, while remaining compliant, and enabling the business. Security tools like DLP, UEBA and CASB aren’t keeping pace. They typically address a single dimension of risk, take months to deploy, and burden security teams with constant fine-tuning. It’s time for a Zero Trust approach to managing and mitigating data risk from insider threats.




Code42 integrates with Okta to automate access controls and provision additional user attributes including department, manager and employment type, in order to reduce Insider Risk exposure, streamline investigations and speed incident response.

Code42 integrates with Palo Alto Networks Cortex XSOAR to accelerate insider threat incident response and automate remediation procedures for potential data exfiltration across computers, email, cloud and SaaS apps.

The Code42 Incydr app for Sumo Logic allows security teams to configure file exposure and exfiltration events into existing Sumo Logic dashboards to detect and respond to Insider Risk.
“If it wasn’t for the Code42 ability to actually see the files, we wouldn’t really understand what the person is doing... it provides us both speed and thoroughness of investigations.”
– Tim Briggs, Director of Incident Response and eDiscovery at Crowdstrike



